FENC had been approved by the board of directors on 2022/11/09 to establish a Chief Information Security Officer, an information security department and its Information & Technology Center (ITC) in charge of the information security management of the Company. In order to achieve efficient management and proper maintenance to the computer information environment, as well as to ensure the confidentiality, completeness and availability of the information access and operation, ITC has established the Information Security Policy and obtained certifications including ISO 27001 - information security standard (certification period: 2022/09/10~2025/09/09) as the guidance for all related personnel to reduce any impact from any information security incidence. The scope covers information authorization, data backup, system development, contractor management and intellectual property management, etc.
FENC has established a well-defined information security management system (hereinafter referred to as ISMS) and policies to protect its competitive advantages, i.e., technological innovation and excellence throughout the industrial chain from downstream to upstream, and honor its commitment to shareholders, customers and partners. The Company has set up ISMS mechanisms and guidelines that apply in various dimensions, including, personnel, operation, technology and legal compliance. It continues to reinforce the management system and technologies and implements a thorough risk control program to effectively safeguard the security of information and resources and ensure digital transformation be undertaken in the organization smoothly, systematically and consistently and that FENC’s goals in information security management be achieved. Simultaneously FENC has keep assessing the potential insurance plan for the information security.
The Company started to implement ISO 27001 in 2014. Information security risks were assessed and ranked in terms of impact, probability, and treatment cost. An internal audit, including PDCA – Plan, Do, Check, and Act cycle, was conducted. ISO 27001 key performance indicators (KPIs) were established to measure the operating effectiveness of the ISMS. Since 2016, the Company has been ISO 27001 certified by an external auditor. It also makes timely adjustments in the allocation of resources to safeguard the security of production processes, protect customer information, sustain business operations and implement ISMS standards effectively.
Security policies and organizations; human resources and information assets; access control and password policies; system acquisition, development and maintenance; communications security; physical and environmental security; information security of the production process; operations security; management of supply chain relationships; management of security incidents; business continuity management; compliance management and management of business process and information system
The Company has joined Taiwan CERT/CSIRT Alliance and established security incident management procedures that specify the process and measures to follow, including the incident reporting protocol and the description of the designated manager’s responsibilities. In the event of an incident, the incident management team confirms the situation and then determines its severity. Next, they initiate the reporting process, handle the incident and track the progress of risk management until the case is closed. The team handling the incident is responsible for making subsequent improvement, reporting work results and putting forth a plan for corrective and preventive actions. FENC has experienced neither major information security incident nor material financial loss induced by such an incident within the scope of audit for ISO 27001 compliance in the past year as of the day this report goes to print.
The Company designates the Human Resources Development Center to organize trainings on information security to promote understanding and raise awareness of its importance among employees. They are encouraged to participate in the training and acquire certificates. System developers and managers are required to comply with the regulations for system establishment and security management to ensure the stability, safety and efficiency of our systems and also to effectively reduce the risk posed by unauthorized access.
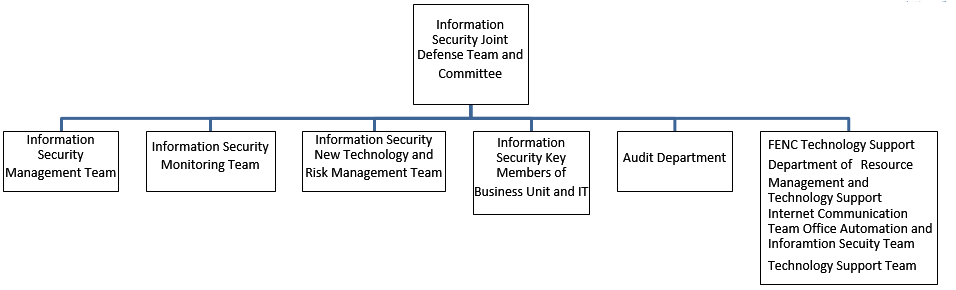
At the production sites, there are designated staff responsible for operation technology and information technology. Additionally, a third party, DDMC, has been involved in part of the structuring of the Company’s information/communication security organization and other related matters, which are handled by a staff of 37 employees. On 2022/11/09, FENC establish an information security department, a functional organization at the board level, with 7 employees which are responsible for building an architecture for corporate information security management and briefing the Company at the monthly risk management meeting on risk-related issues, corresponding responses, security-strengthening measures and review of regulations.
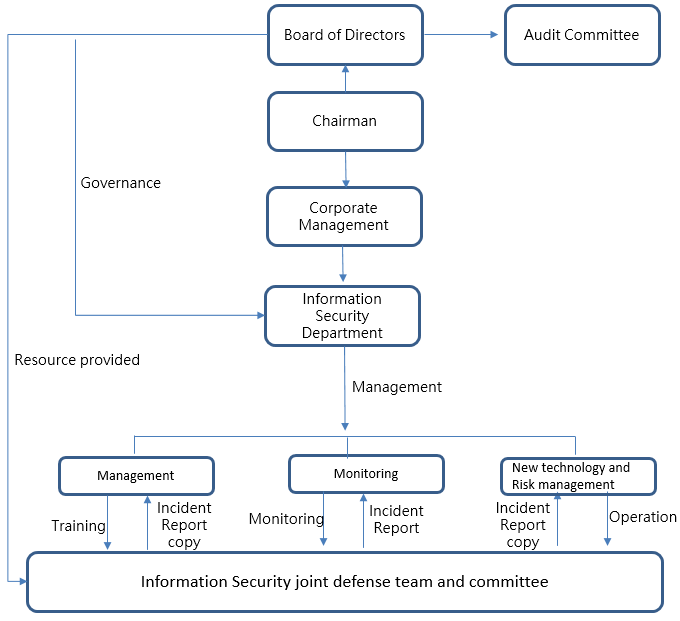
The Company’s Information Security Committee oversees the implementation of corporate security policies and is entrusted with the management and promotion of IT security, information security of the production process, business continuity and other security-related issues. The Committee is tasked with the following duties:
1. Security operations: Analyzing security threats in a timely manner.
2. Cyber intelligence: Assisting the Board of Directors to understand potential security concerns.
3. Data protection: Preventing employees’ abuse or theft of data.
4. Security structure: Ensuring that IT and network infrastructure be designed in such a way that its security is guaranteed.
5. Supply chain information security:To comply with customer information security requirements and communicate the latest information security regulations and precautions to suppliers.
1-2 Records l Total 2 Records
Tel:+886-2-27338000 #8969
Fax:+886-2-27367184
TEL:+886-2-27338000 #8735
FAX:+886-2-27368175
Please refer to FENC Speak-up policy
https://cg.fenc.com/upload/cg/cg_20220520002.pdf
The internal complaint channel is provided in accordance with Paragraph 3 of Article 13 of the Act of Gender Equality in Employment.